Database Secure Configuration Review
- Home
- About Us
- Services
- Cyber Network Defense
- Database Secure Configuration Review
With data breaches growing every day along with the evolving set of data protection and privacy regulations, protecting business sensitive and regulated data is mission critical. However, knowing whether the database is securely configured, who can access it, and where sensitive personal data resides is a challenge for most organizations.
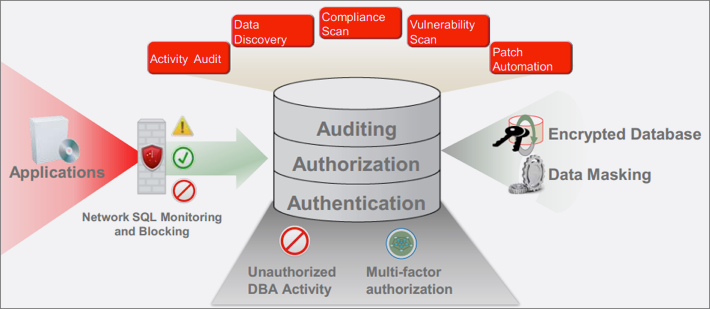
Corporate databases contain sensitive and confidential information which should be protected with the highest priority. Attackers typically spend considerable time understanding their target. They may use several tools that automate the discovery of databases, open ports, known vulnerabilities, and sensitive user accounts.
They may then launch various attacks including password theft, brute force password cracking, privilege escalations, and SQL injection attacks. Once they finish probing, they identify the weakest links and then determine their next steps. In essence, the attackers first evaluate the current security status to find the easiest way to get to the sensitive data without being caught.
Database security assessment will help you determine the protection level of your databases and steps to be taken for further security hardening.
Applicable databases:
- SQl2005
- SQl2008 & latest
- MySQL
- Oracle 10
- Oracle11g
- IBM DB2
- PostgreSQL
- Informix
- Sybase
Cyber Network Defense
CICRA Consultancies In Brief
- 10+ years in Cyber Security
- Local & Foreign cybersecurity engagements (Europe, Mideast, Oceania Regions)
- Local & Foreign cybersecurity engagements in Banking Sector
- Globally Accepted Methodologies for engagements
- Diversified industry experience
- The Right Team with the right qualifications

